Artificial Intelligence in Cybersecurity
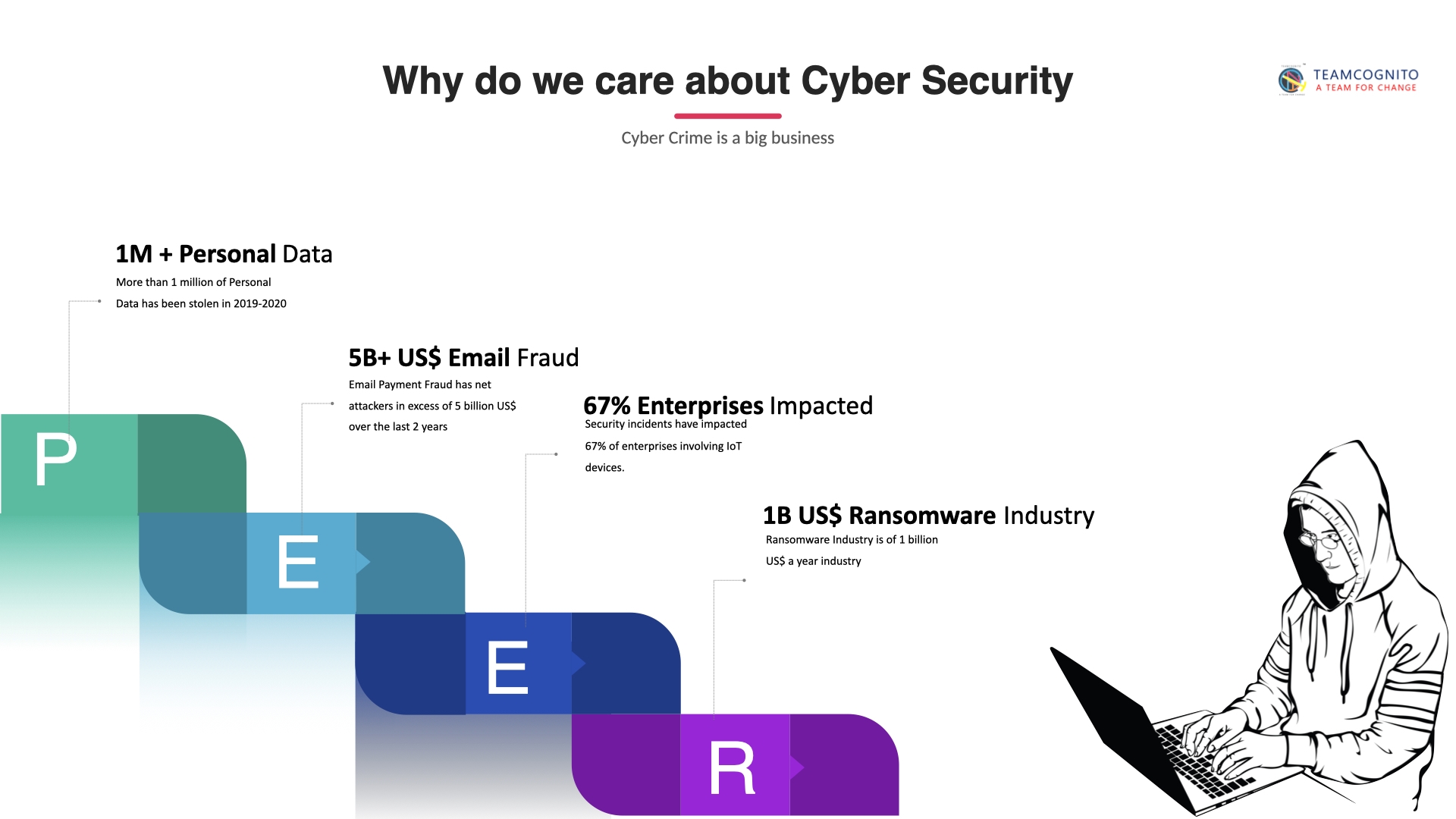
With the introduction of AI in all market segments, this technology has resulted in significant changes in cybersecurity, thanks to machine learning. In the development of automated security systems, natural language processing, face recognition, and automatic threat detection, AI has played a critical role. It’s also being used to create smart malware and attacks to get around the most up-to-date data security protocols. Threat detection systems with AI can predict attacks and alert administrators to any data breaches instantly, making them the next cybersecurity trend in 2021.
Automotive Hacking and its Influence
In 2021, the first cybersecurity theme will be the rise of automotive hacking. In areas including cruise control, engine timing, door lock, airbags, and advanced driver support systems, modern cars are outfitted with automated software that provides smooth communication for drivers. These vehicles communicate via Bluetooth and Wi-Fi, exposing them to a variety of vulnerabilities and hacker threats. We believe that taking control of the vehicle or using microphones for eavesdropping will increase in 2021 as the use of autonomous vehicles grows. Self-driving or autonomous cars use a more complex mechanism that causes more rigorous cybersecurity protections.
Mobile malware is the new threat
We observed mobile banking malware or attacks increasing by 50% in 2019, making our handheld devices a target for hackers. Individuals are more at risk from all of our images, financial transactions, emails, and texts. In 2021, a smartphone virus or malware could attract the attention of cybersecurity trends.
Cloud computing vulnerabilities
To avoid data leaks, security protocols must be continuously monitored and updated as more companies migrate to the cloud. Although cloud applications like Google or Microsoft are well-protected on their end, user error, malicious apps, and phishing attacks continue to be a major source of erroneous errors, malicious apps, and phishing attacks.
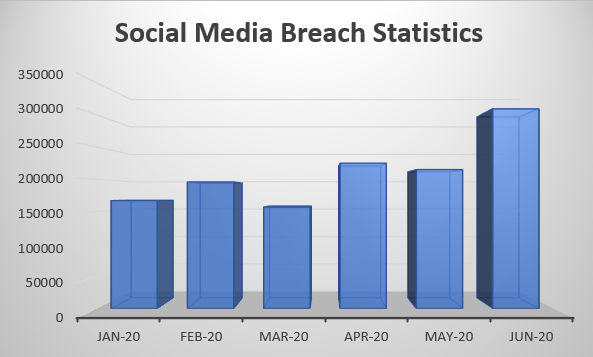
Data breaches and their effect
Data will continue to be a challenge for businesses all over the world. The primary goal right now is to protect digital data, whether it belongs to an individual or an entity. Hackers can gain access to personal data by exploiting some minor flaw or bug in your system browser or software. The General Data Protection Regulation (GDPR) went into force on May 25, 2018, granting data protection and privacy to individuals in the European Union (EU). Similarly, on January 1, 2020, the California Consumer Privacy Act (CCPA) went into effect to protect consumer rights in California.
IoT and 5G Network
IoT with 5G networks is the next big cybersecurity theme for 2021. With 5G networks set to launch internationally in 2020, the Internet of Things will usher in a new age of interconnectivity. This contact between multiple devices exposes them to outside influence, threats, or an unknown software error, exposing them to vulnerabilities. Even Google Chrome, the world’s most popular browser, was found to have serious flaws. 5G architecture is still relatively new in the industry, and it will take a lot of investigation to find flaws that will enable the system to be safe against external attack. Every step of the 5G network might bring a plethora of network attacks we might not be aware of.
State-Sponsored Cyber Warfare
There will be no truce between the western and eastern forces in their search for dominance. Though the attacks are rare, they have a major effect on an event such as elections. With over 70 elections expected this year, illegal activity will probably increase during this time. The biggest cybersecurity trends for 2021 are likely to be high-profile data hacks, political and industrial secrets.
Insider Threats
One of the most common causes of data breaches is human error. An entire company can be brought down by a single bad day or a deliberate loophole that allows millions of records to be stolen. Employees were directly or indirectly responsible for 34% of total attacks, according to a Verizon data breach report. As a result, raise awareness among employees to ensure that data is protected in every way possible.
How TeamCognito can help?
The best call today is to step up your security game and keep up with these cybersecurity trends, and we will help. TeamCognito’s cybercrime experts in Kolkata will help you stay one step ahead in this rapidly developing sector. With our proactive approach, you’ll have access to approaches of protecting your infrastructures, securing data and information, conducting risk analysis and mitigation, architecting cloud-based protection, achieving compliance, and much more.
TeamCognito has become one of the leading cybersecurity company in Kolkata. From receiving Special Recognition from the Ministry of Information Technology of the Government of India for the Citizens Voice Challenge to being incubated by BCC&I. With 60+ clients, including international clients, we’re going global. You can be assured that you will receive top-notch service.
About TeamCognito
Cybersecurity, Machine Learning, and Artificial Intelligence are among our specialities. When things get technical, TeamCognito also has experience in Application, Website, and Product Creation, as well as Digital Marketing services to help you make a mark in the media. We provide the top cybersecurity company in Kolkata.
TeamCognito is a brand that stands for “The Best of All.” Growing to be one of India’s Top 10 Cybersecurity Service Providers and the one-stop shop for all your company needs, from apps to web to marketing.
Even after taking the best protection measures, there is a chance your mobile data can be breached, that is where TeamCognito can come into being. TeamCognito’s cloud-native, purpose-built solutions for Salesforce, Office365 and G Suite will give full protection to your organisation data. With TeamCognito’s cybersecurity services in Kolkata, you will stay protected all the time.
Low-cost cyber security solutions – Secure and protect your data
TeamCognito makes use of artificial intelligence to segregate the critical tasks from the routine network activity. We have the finest cybersecurity experts in Kolkata who can assist in identifying the critical cyber threats, thus helping teams save time that might otherwise be spent investigating alerts that do not need immediate attention. We try to identify the chains of activities that are responsible for the cyber-attacks and then take action accordingly.
Automotive hacks become an ever-growing concern for every business today. At TeamCognito, avail affordable, comprehensive cybersecurity solutions for your automotive hacks. Our cybersecurity consultant services in Kolkata will protect all the sensitive data, meet compliance requirements, so that you can remain safeguarded and stress free.
We are the industry leader in cyber security solutions, some of the renowned companies of Kolkata are dependent on us. Our cyber security experts have tons of experience in handling mobile malware mitigation issues. This wide range of experience provides us with unparalleled insight into new malware threats before they cause significant damage.
Unauthorized cloud services can result in an increase in malware infections or data exfiltration. With TeamCognito’s top cybersecurity services stay protected from all the five kinds of cloud security vulnerabilities – account hijacking, malicious insiders, data breaches, system vulnerabilities and insecure APIs.
Data leaks can prove fatal if no actions are taken at the right time. Be it any business organisation, government agencies or individuals, get total safety and security. TeamCognito being one of the premium cyber security solutions companies in Kolkata is committed to helping people stay safe online and beyond. Discover how our award-winning security can help you stay protected against data breaches 24×7.
We offer comprehensive protection for the critical infrastructure and OT environments. Enjoy complete protection on home networks on Wifi router with our top-notch cyber security services in Kolkata. Get the latest products and solutions to secure Internet of Things (IoT) and 5G for your business, school campus, or vehicle from TeamCognito.
Cyberwarfare has become a potential threat in India in recent times. If your agency is the victim of any computer viruses or denial-of-service attacks, look no further, get in touch with TeamCognito, get best recommendations on methods of defending against the damaging effects of cyber warfare on a nation’s digital infrastructure.
Potential risks of insider threats are numerous, including installing malware, financial fraud, data corruption, or theft of valuable information. To counteract all these possible scenarios, organizations should implement an insider threat solution. Decrease your risk immediately with advanced insider threat detection and prevention from TeamCognito.